Managing Supply Chain Cyber Risks

Evolving Insurance Ecosystem
Insurance industry is fast evolving with forward looking insurers increasingly adopting futuristic technologies such as blockchain, big data, analytics and Robotic Process Automation (RPA) etc. to improve pricing, boost profitability, simplify business process and undertake value-driven decision making. Insurance organisations are finding new digital channels such as Internet of Things (IOT), social media and mobiles to interact with customers. In order to achieve this, insurance organisations are now changing their operating models to embrace more outsourcing and involvement from specialist and niche service providers.
Figure 1: Insurance Eco-System

An insurance organisation of today, must deal with a complex network of third parties and fourth parties who carry out numerous critical activities for the organisation. These third parties could be in the form of partners, subsidiaries, suppliers or even fourth parties. Organisations now rely on third parties for conducting data analysis on sensitive customer data to gain valuable insights on their customers, maintaining and operating critical business processes such as fraud detection systems, underwriting etc., managing critical tasks through bots and managing customer engagement.
This increased dependency on third parties has altered the cyber threat landscape of insurance organisations. Our analysis based on open source threat intelligence indicates that cyber-attacks through third parties (supply chain attacks) on financial services organisations have increased three-fold in the last 12 months. Also, security researchers have identified that supply chain attacks in 2019 have increased by 78%1. In the last six months, major cyber-attacks on organisations such as Asus2 and Wipro3 have emphasized the criticality of supply chain attacks.
Increasing criticality of third-party cyber risks
According to our analysis, supply chain attacks is now the second most prevalent attack vector on financial services organisations after social engineering or phishing attacks. The severity and frequency of supply chain attacks have increased in 2019. Our analysis indicates that there are three main reasons for the increase in supply chain attacks.
Figure 2: Reasons for the increase in supply chain attacks

Focus on economic and industrial espionage by nation state actors: Nation state actors are highly funded, well-resourced and technically sophisticated attackers who often work for a government to disrupt or compromise target governments, organisations or individuals to gain access to valuable data or intelligence. Economic and industrial espionage has become the key objective for most nation state actors. As third parties move up the value chain carrying out critical activities for insurance organisations, these third parties are increasingly becoming the target of sophisticated nation state actors. Often these third parties do not have mature cyber security capabilities and organisations do not enforce same levels of controls on these third parties. Hence third parties become easy targets for nation state actors to gain access to sensitive data, intelligence or access to the organisation itself.
Increasingly interconnected nature of systems: As Insurtech evolves, third parties now have multiple touchpoints with the insurance organisation’s network and infrastructure. In many cases these touchpoints are not controlled or protected effectively by the organisation. In several instances, it has become a challenge for organisation’s to have visibility over the third-party touchpoints. Threat actors see these touchpoints as an opportunity to exploit the organisation.
Organisations slow to adapt new best practices: Most insurance organisations have standard practices for classifying and assessing third parties. These processes are conducted annually or while the third party is onboarded. These measures are in-adequate and do not address the evolving cyber threat landscape of insurance organisations.
- Third party assessments are checklist based and do not test the operational effectiveness of the third party’s cyber security
- Managing third party risks requires streamlined coordination between legal, procurement, risk, IT and cyber security departments within an organisation. The lack of coordination hinders consistent implementation of third-party controls that matches with their cyber threat
- Third party assessments are conducted once every year and organisations do not continuously monitor the third parties to check if the threat landscape has
- Existing technology platforms for managing third-parties are considered inadequate
A holistic approach to managing third party risks
As organisations are compelled to catch up with the ever-evolving cyber threat landscape, a holistic approach to third party management is required to manage cyber risks. The approach must consistently manage cyber risks across the life cycle of the third party.
Figure 3: Cyber security processes across the supply chain lifecycle
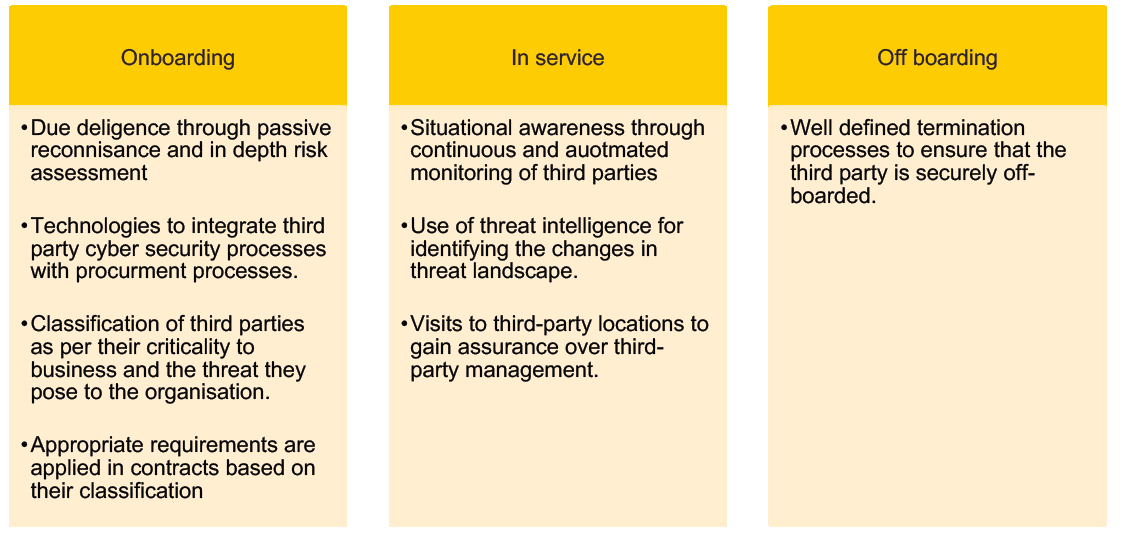
Due diligence: Cyber due diligence helps to accurately evaluate the third party’s information assets and therefore the business as a whole. Organisations understand variety of issues, including how an attacker views the target, whether threat actors are using the third party’s systems and obvious vulnerabilities. This enables organisations to understand the risk they are acquiring by partnering with a third party.
Third party classification: Several factors need to be considered when classifying third parties ranging from their access to organisation’s crown jewels, regulatory requirements, the impact to business if they were compromised, number of touchpoints with the organisation, profile of the third party’s other clients, fourth parties (suppliers of suppliers) and their cyber security maturity etc.
A key challenge for the cyber security teams is gaining visibility over procurement processes and when a third party is being on-boarded. This can be achieved by technologically integrating procurement processes with cyber security third party management software.
Situational awareness: Situational awareness is an understanding of threats and how those threats can change over time or with the fluctuation of environmental variables. For cybersecurity teams, situational awareness means understanding the threats to organisation’s crown jewels and its impact to the organisation.
By integrating operational & tactical threat intelligence with third party management processes, insurance organisations can always maintain situational awareness of their third-party cyber risks.
During off-boarding, legal, technological, procedural and assurance processes must be in place to ensure that the organisation’s data is removed from the third party.
How can Transformationplus Assist
Transformationplus is an Australian start up specializing in niche cyber security domains such third party risk management, threat intelligence, travel cyber security, regulatory compliance and incident response services.
Through insight, intelligence and technology, we help finance and insurance organisations manage their third- party risks. We help organisations answer the following questions:
- What is the cyber threat landscape of your organisations?
- What are your organisation’s third-party cyber risks?
- How can your organisation continuously integrate threat intelligence to monitor the third parties for situational awareness?
- How can your organisation integrate due diligence processes when a new third party is on-boarded?
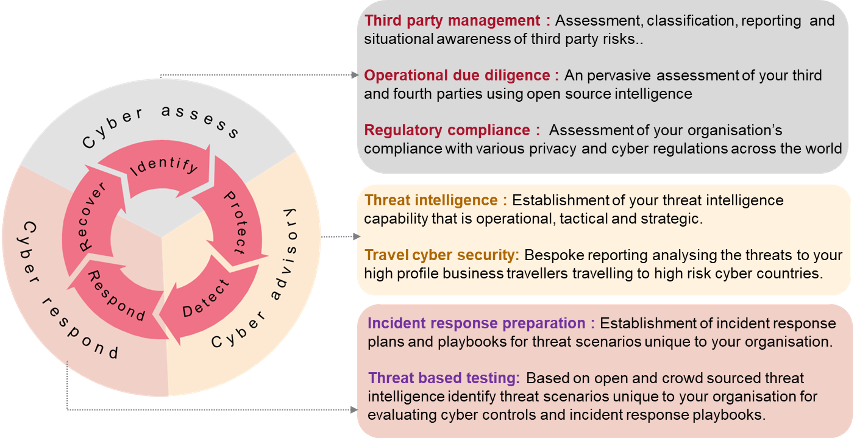
Our Cyber Security Service Offerings